Session hijacking or cookie hijacking is a way to exploit a valid computer session and gain unauthorised access to information or services in a computer system. It mostly refers to the theft of HTTP cookies that are used to authenticate a user on a web server. In this article, I am going to show you how to perform session hijacking on a website running on WordPress.
Preparation
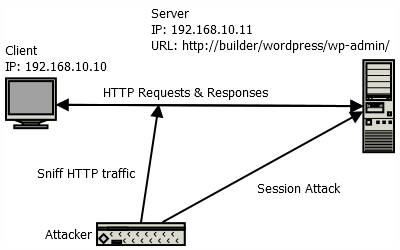
You will need a client computer with a browser and a web server installed with WordPress. An attacker PC, installed with Wireshark, is used to sniff the HTTP packets between the client and the server. The network is summarised in the diagram below. To sniff packets on the attacker PC, you may need to configure port mirroring on your LAN switch. If that’s too much of a hassle, you can opt to use the client PC as the attacker PC instead.
Step 1 – Logon to website
The first step is to logon to the WordPress admin site from the client PC. Once the server has verified the logon credentials, it will send some HTTP cookies to the client. From this point onwards, any HTTP requests made from the client to the server WordPress admin site will now include the cookie information.
Step 2 – Sniff HTTP Traffic and Extract Cookies
Sniff the packets from the attacker PC using Wireshark and filter for “http.cookie“. You will see packets similar to the one below. For the packet below, the client PC is making a HTTP GET to the server with the cookie information that we need.
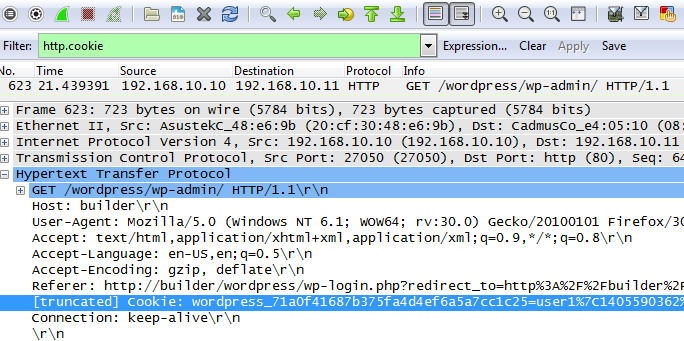
Copy the cookie information by performing a right-click on the cookie field and select Copy->Value. Paste the values in a text editor. Each cookie is terminated by a “;” character. Replace the “;” character with a new line so that you will have one cookie per line. Each line consists of a cookie name and a cookie value pair that is separated by an “=” (equals) sign. Filter out the three cookies shown below. The hashes in the cookie names shown below are unique and will most probably be different from yours.
|
1 2 3 |
wordpress_71a0f41687b375fa4d4ef6a5a7cc1c25=user1%7C1405590362%7Cce6848b5e7d6ae991f24a89f0fbb20fa wordpress_test_cookie=WP+Cookie+check wordpress_logged_in_71a0f41687b375fa4d4ef6a5a7cc1c25=user1%7C1405590362%7Ce55040de366f539ce31a640881ef691f |
Step 3 – Hijack Session
On the attacker PC, launch Chrome browser and install the EditThisCookie extension to modify the cookies.
Navigate to the WordPress admin site from Chrome browser and it will redirect you to the login page. Now use the EditThisCookie extension to add all the three missing cookies.
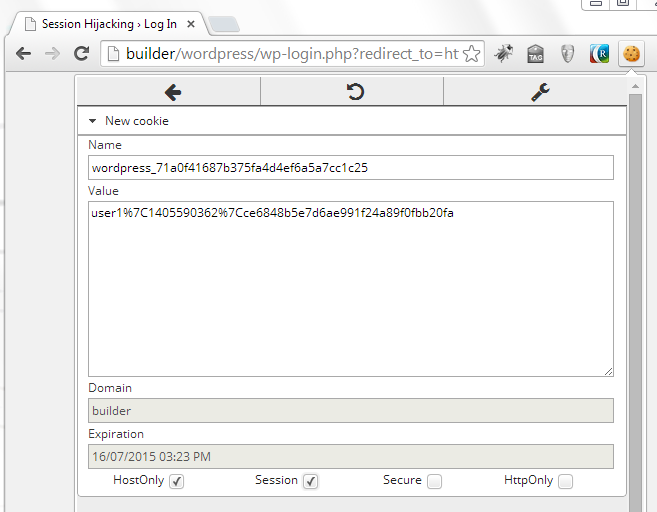
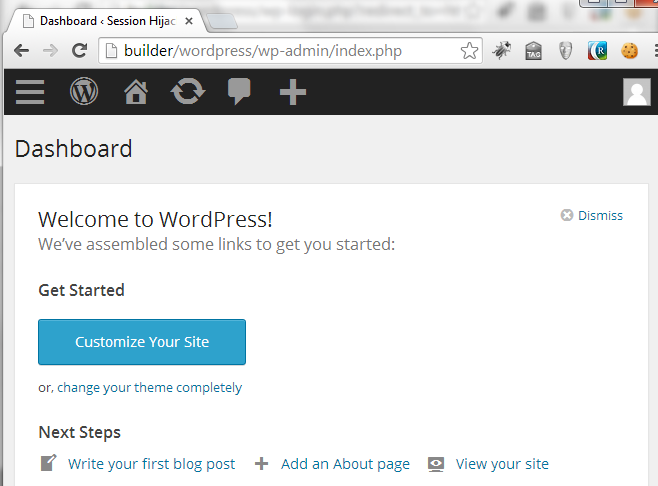
Once the cookies have been added and verified, try to access the WordPress admin site again. This time, you should be logged in!
Notes
Instead of trying to capture the cookies from Wireshark, you can also steal the cookies from the browser on the client PC.
This method of session hijacking only works on HTTP and not on HTTPS (or SSL/TLS) sites.

